What is Kerberos?
Kerberos is an authentication protocol that works on the basis of tickets that allows clients to connect to services over an insecure network and still allow clients to prove their identity in a secure manner.
The steps described below are a compilation of what I found when reading on Kerberos. Feel free to share your comments!
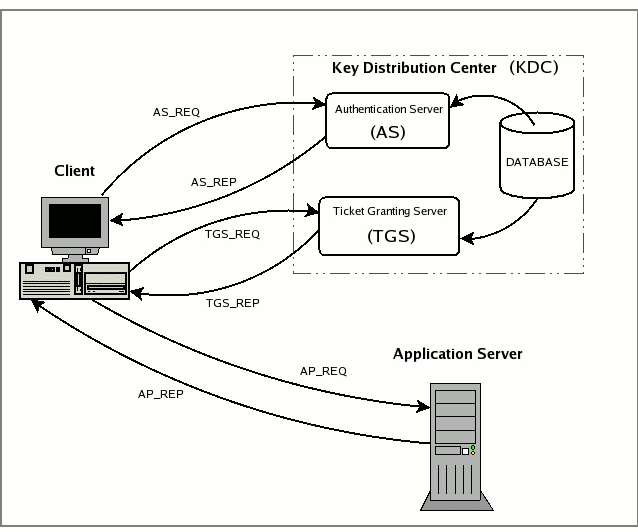
Key Distribution Center (KDC)
The authentication server in a Kerberos environment, based on its ticket distribution function for access to the services, is called Key Distribution Center or more briefly KDC. Since it resides entirely on a single physical server (it often coincides with a single process) it can be logically considered divided into three parts: Database, Authentication Server (AS) and Ticket Granting Server (TGS).
Database
The database is the container for entries associated with users and services. We refer to an entry by using the principal (i.e. the name of the entry) even if often the term principal is used as a synonym for entry. Each entry contains the following information:
- The principal to which the entry is associated;
- The encryption key and related kvno;
- The maximum validity duration for a ticket associated to the principal;
- The maximum time a ticket associated to the principal may be renewed (only Kerberos 5);
- The attributes or flags characterizing the behavior of the tickets;
- The password expiration date;
- The expiration date of the principal, after which no tickets will be issued.
In order to make it more difficult to steal the keys present in the database, the implementations encrypt the database using the master key, which is associated with the principal K/M@REALM. Even any database dumps, used as backups or for propagation from the KDC master towards the slave, are encrypted using this key, which it is necessary to know in order to reload them.
Authentication Server (AS)
The Authentication Server is the part of the KDC which replies to the initial authentication request from the client, when the user, not yet authenticated, must enter the password. In response to an authentication request, the AS issues a special ticket known as the Ticket Granting Ticket, or more briefly TGT, the principal associated with which is krbtgt/REALM@REALM. If the users are actually who they say they are (and we'll see later how they demonstrate this) they can use the TGT to obtain other service tickets, without having to re-enter their password.
Ticket Granting Server (TGS)
The Ticket Granting Server is the KDC component which distributes service tickets to clients with a valid TGT, guaranteeing the authenticity of the identity for obtaining the requested resource on the application servers. The TGS can be considered as an application server (given that to access it it is necessary to present the TGT) which provides the issuing of service tickets as a service. It is important not to confuse the abbreviations TGT and TGS: the first indicates a ticket and the second a service.
Tkt Granting service: Ticket Granting Service.
Centos's HTTP: The service the user wants to access.
Black Smile: User (user principle)
Black Spider Web: Service ID (http service principle)
Black key: User hashed password.
Green key: TGS Secret Key.
Red key: Client/TGS Session Key.
Blue key: Service secret key (HTTP)
Orange key:: Client/Server Session Key.
Black chest: Contain Session Key
Green chest: Ticket-Granting-Ticket.
Blue chest: Client-to-server Ticket.
Purple chest: Unencrypted service id and timestamp
Kerberos Packets:
Note unencrypted data in round brackets (), and encrypted data in curly brackets {}: ( x, y, z ) means that x, y, z are unencrypted; { x, y, z }K indicates that x, y, z are encrypted all together using the symmetrical key K.
AS_REQ is the initial user authentication request (i.e. made with kinit) This message is directed to the KDC component known as Authentication Server (AS);
AS_REQ = ( PrincipalClient , PrincipalService , IP_list , Lifetime )
AS_REP is the reply of the Authentication Server to the previous request. Basically it contains the TGT (encrypted using the TGS secret key) and the session key (encrypted using the secret key of the requesting user);
TGT = ( PrincipalClient , krbtgt/REALM@REALM , IP_list , Timestamp , Lifetime , SKTGS )
AS_REP = { PrincipalService , Timestamp , Lifetime , SKTGS }KUser { TGT }KTGS
TGS_REQ is the request from the client to the Ticket Granting Server (TGS) for a service ticket. This packet includes the TGT obtained from the previous message and an authenticator generated by the client and encrypted with the session key;
Authenticator = { PrincipalClient , Timestamp }SKTGS
TGS_REQ = ( PrincipalService , Lifetime , Authenticator) { TGT }KTGS
TGS_REP is the reply of the Ticket Granting Server to the previous request. Located inside is the requested service ticket (encrypted with the secret key of the service) and a service session key generated by TGS and encrypted using the previous session key generated by the AS;
TService = ( PrincipalClient , PrincipalService , IP_list , Timestamp , Lifetime , SKService )
TGS_REP = { PrincipalService , Timestamp , Lifetime , SKService }SKTGS { TService }KService
AP_REQ is the request that the client sends to an application server to access a service. The components are the service ticket obtained from TGS with the previous reply and an authenticator again generated by the client, but this time encrypted using the service session key (generated by TGS);
Authenticator = { PrincipalClient , Timestamp }SKService
AP_REQ = Authenticator { TService }KService
AP_REP is the reply that the application server gives to the client to prove it really is the server the client is expecting. This packet is not always requested. The client requests the server for it only when mutual authentication is necessary.
AP_REP = Authenticator { PrincipalService, Timestamp }SKService
Centos's HTTP: The service the user wants to access.
Black Smile: User (user principle)
Black Spider Web: Service ID (http service principle)
Black key: User hashed password.
Green key: TGS Secret Key.
Red key: Client/TGS Session Key.
Blue key: Service secret key (HTTP)
Orange key:: Client/Server Session Key.
Black chest: Contain Session Key
Green chest: Ticket-Granting-Ticket.
Blue chest: Client-to-server Ticket.
Purple chest: Unencrypted service id and timestamp
AS_REP = { PrincipalService , Timestamp , Lifetime , SKTGS }KUser { TGT }KTGS
TGS_REQ = ( PrincipalService , Lifetime , Authenticator) { TGT }KTGS
TGS_REP = { PrincipalService , Timestamp , Lifetime , SKService }SKTGS { TService }KService
AP_REQ = Authenticator { TService }KService
How does Kerberos work?
These are the steps necessary for a client to obtain an authenticated and verified request to a service (for example a web HTTP service).
Step 1: Login
The user enters the username and password. In some cases you only have to enter the password in step 5. The client will then transform the password into a client secret key(KUser).
Step 2:
Initial authentication request, the client (kinit) asks the KDC (more specifically the AS) for a Ticket Granting Ticket.
The client sends a plaintext message to the authentication server. This message contains
- username;
- the name of the requested service (in this case this is the Ticket Granting Server – TGS);
- the network address;
- the requested lifetime of the TGT.
Note that no secret information (client secret key or password) is sent).
The client sends a plaintext message to the authentication server. This message contains
Step 3:
Server checks if the user exists
The server receives the message and will check if the username exists in the Key Distribution Center – KDC. Again this is not a credential check but only a check to verify that the user is defined. If all is OK the server proceeds.
The server receives the message and will check if the username exists in the Key Distribution Center – KDC. Again this is not a credential check but only a check to verify that the user is defined. If all is OK the server proceeds.
Step 4:
Server sends TGT back to the client
The server generates a random key called the session key( SKTGS) that is to be used between the client and the TGS.
The authentication server then sends back two messages (i.e the chest boxes )to the client
- Message A is encrypted with the client secret key(KUser). The client secret key is not transferred but is retrieved from the password (more to speak the hash) found in the user database. This happens all on the server-side. The message contains
- TGS name;
- timestamp;
- lifetime;
- the TGS session key (the key generated at the beginning of this step( SKTGS)).
- Message B is the Ticket Granting Ticket, encrypted with the TGS secret key(KTGS), that contains
- your name;
- the TGS name;
- timestamp;
- your network address;
- lifetime;
- the TGS session key ( SKTGS)(same as in message A).
The server generates a random key called the session key( SKTGS) that is to be used between the client and the TGS.
- TGS name;
- timestamp;
- lifetime;
- the TGS session key (the key generated at the beginning of this step( SKTGS)).
- your name;
- the TGS name;
- timestamp;
- your network address;
- lifetime;
- the TGS session key ( SKTGS)(same as in message A).
Step 5:
Enter your password
The client receives both messages and then requests the user for the password. In some cases, this is already done in the first step. The password is then converted (hash) to the client secret key(KUser). Note that this key was also generated on the server-side in the previous step.
The client receives both messages and then requests the user for the password. In some cases, this is already done in the first step. The password is then converted (hash) to the client secret key(KUser). Note that this key was also generated on the server-side in the previous step.
Step 6:
Client obtains the TGS Session Key
The client now uses the client secret key(KUser) to decrypt message A. This gives the client the TGS Session key( SKTGS).
The client can not do anything with message B (the TGT) for the moment as this is encrypted with the TGS secret key(KTGS) (which is only available at the server-side). This encrypted TGT is stored locally in the credential cache.
The client now uses the client secret key(KUser) to decrypt message A. This gives the client the TGS Session key( SKTGS).
Step 7:
Client requests server to access a service
The client now prepares two messages (i.e the chest boxes )to be sent to the server
- Message C( Wireshark trace has a more elaborate explanation) is an unencrypted message that contains
- the service that the client wants to access;
- the lifetime;
- message B or the TGT (this TGT itself is encrypted and included in the unencrypted message send to the server).
- Message D is a so-called Authenticator encrypted with the TGS session key( SKTGS) and contains
- your name;
- timestamp.
The client now prepares two messages (i.e the chest boxes )to be sent to the server
- the service that the client wants to access;
- the lifetime;
- message B or the TGT (this TGT itself is encrypted and included in the unencrypted message send to the server).
- your name;
- timestamp.
Step 8:
Server verifies if service exist
The server first verifies if the requested service exists in the KDC. If this is the case, it will proceed.
The server first verifies if the requested service exists in the KDC. If this is the case, it will proceed.
Step 9:
Server verifies request
The server now extracts the content of message B (the TGT) from message C and then decrypts that message B (the TGT) with its TGS secret key(KTGS). This will give the server the TGS session key( SKTGS). This is a shared key between the client and the server.
With this TGS session key( SKTGS), the server is now able to also decrypt the message D.
The server now has your name and timestamp from message D and a name and timestamp from message B. The server will then
- Compare both name and timestamp in both values;
- Check if the TGT is expired (the lifetime field in the TGT);
- Check that the Authenticator is not in the cache (to prevent replay).
If all checks turn out OK, the server continues.
The server now extracts the content of message B (the TGT) from message C and then decrypts that message B (the TGT) with its TGS secret key(KTGS). This will give the server the TGS session key( SKTGS). This is a shared key between the client and the server.
Step 10:
Server generates a service session key(SKService)
The server generates a random service session key(SKService). It will then send two messages to the client.
- Message E: the service ticket that is encrypted with the service secret key(KService) and contains
- your name;
- the service name;
- timestamp;
- your network address;
- lifetime;
- the service session key(SKService).
- Message F: encrypted with the TGS session key( SKTGS) containing
- service name;
- timestamp;
- lifetime;
- service session key(SKService).
The server generates a random service session key(SKService). It will then send two messages to the client.
- your name;
- the service name;
- timestamp;
- your network address;
- lifetime;
- the service session key(SKService).
- service name;
- timestamp;
- lifetime;
- service session key(SKService).
Step 11:
Client receives a service session key
Because the client has the TGS session key( SKTGS) cached from previous steps it can now decrypt message F to obtain the service session key(SKService). It is however not possible to decrypt the service ticket (message E) because that one is encrypted with the service secret key(KService).
Because the client has the TGS session key( SKTGS) cached from previous steps it can now decrypt message F to obtain the service session key(SKService). It is however not possible to decrypt the service ticket (message E) because that one is encrypted with the service secret key(KService).
Step 12:
Client contacts service (HTTP server)
Now it’s time for the client to contact the service. Again two messages are send
- Message G: a new authenticator message encrypted with the service session key(SKService) that contains
- your name;
- timestamp.
- Message E: the previously received message E, that is still encrypted with the service secret key(KService)
Now it’s time for the client to contact the service. Again two messages are send
- your name;
- timestamp.
Step 13:
Service receives the request
The service then decrypts the message E with its service secret key(KService) to obtain the service session key(SKService)
The service will then use that newly obtain service session key(SKService) to decrypt the authenticator message G.
The service then decrypts the message E with its service secret key(KService) to obtain the service session key(SKService)
Step 14:
Service verifies the request
Similar to step 9, the service then does some verification
- Compare the user name from the authenticator (message G) to the one in the ticket (comparing message E);
- Compare the timestamp in message G with the timestamp in the ticket (message E);
- Check if the lifetime (message E) is expired;
- Check that the authenticator (message G) is not already in the cache, to prevent replay attacks.
If all checks turn out OK, the service continues.
Similar to step 9, the service then does some verification
Step 15:
Service confirms identity to the client
The service will then confirm its identity to the client
- Message I: an authenticator message encrypted with the service session key(SKService) that contains
- the id of the service;
- timestamp.
The service will then confirm its identity to the client
- the id of the service;
- timestamp.
Step 16:
Client receives confirmation
The client then receives the authenticator message I and decrypts its with the cache service session key(SKService) (obtained in step 11). This allows the client to know the id of the service and if the timestamp is valid. If everything is OK the client can proceed.
The client then receives the authenticator message I and decrypts its with the cache service session key(SKService) (obtained in step 11). This allows the client to know the id of the service and if the timestamp is valid. If everything is OK the client can proceed.
Step 17:
Client communicates with the service
The authentication and verification are finished. The client can now talk to the service. Note that this only involves the authentication and verification of a service. This process will not decide if the client is actually allowed to do the requested service. This is something that is decided by the ACLs within the server that provides the service. This is not part of Kerberos.
The authentication and verification are finished. The client can now talk to the service. Note that this only involves the authentication and verification of a service. This process will not decide if the client is actually allowed to do the requested service. This is something that is decided by the ACLs within the server that provides the service. This is not part of Kerberos.
Kerberos packets analysis
Assumptions
- As always, we’ll start with a bunch of assumptions to make sure we are in the same chapter (mostly given up trying to be on the same page).
- There is a lot going on with Kerberos in Windows Domains. Some of it involves proprietary details beyond the scope of the Kerberos 5 protocol that we do not care about in this post. Here we are only interested in the pure-Kerberos details.
- I skip most of the details of what each actor is doing and instead focus on the messages exchanged by the protocol here.
- The network traces captured for this post were generated with Windows Pro 10 running on AWS.
- No effort was made to obfuscate any of the information in these screenshots. All traffic was generated in a test environment that will no longer exist by the time this post is published.
Structure of a Kerberos Ticket
A Kerberos Ticket includes the following information:
- Unencrypted Part:
- Version number of ticket format.
- Service realm
- Service principal
- Encrypted Part:
- Ticket flags*
- Session key
- Client realm
- Client principal (username)
- List of Kerberos realms that took part in authenticating the user to whom this ticket was issued.
- Timestamp and other meta data about last initial request.
- Time client was authenticated.
- Validity period start time (optional).
- Validity period end time.
- Ticket Granting Server (TGS) Name/ID
- Timestamp
- Client (workstation) Address
- Lifetime
- Authorization-data — used to pass authorization data from the principal on whose behalf a ticket was issued to the application service ( see Section 5.3 of RFC4120 for more information)
*The following flags can be used in a ticket:
- reserved(0)
- forwardable(1)
- forwarded(2)
- proxiable(3)
- proxy(4)
- may-postdate(5)
- postdated(6)
- invalid(7)
- renewable(8)
- initial(9)
- pre-authent(10)
- hw-authent(11)
- transited-policy-checked(12)
- ok-as-delegate(13)
We will see two tickets in this example: Ticket Granting Ticket (TGT) and Service Ticket.
Structure of a Kerberos Authenticator
A Kerberos Authenticator contains the following information (all encrypted):
- Timestamp
- client ID
- application-specific checksum
- initial sequence number KRB_SAFE or KRB_PRIV messages)
- session sub-key (used in negotiations for a session key unique to this particular session)
Authenticators must not be re-used. A server that encounters a replayed authenticator must reject the message.
We will see one authenticator in this request: the authenticator sent with the TGT-REQ message.
Domain User Sign-On
The following network packets shows the initial TCP connection between the domain-joined Windows and the domain controller when the user “OFFICE\UserNameX” tried to login. Note, the domain in question is called OFFICE(its DNS name is OFFICE.COMPANY.COM); the domain user we are tracing the sign-in of is called UserNameX”.
Authentication Service Exchange
The first three packets are the typical SYN-SYNACK-ACK handshake that happens for any TCP connection.
The forth packet that is sent from the windows Client to the domain controller (KDC/Authentication Service) is the AS-REQ message (which is a type of KRB_KDC_REQ message). The AS-REQ message looks like the following:
This is AS_REQ (in my original protocol description). You can see the following fields in the trace above:
- pvno — Kerberos protocol version (5).
- msg-type — Application class tag number (10)
- padata — Pre-Authentication data that contains a PA-PAC-REQUEST structure. This is mentioned briefly in RFC4120, but this goes into much more detail
- kdc-options — flags requested for the resulting ticket (forwardable, renewable, canonicalize, renewable-ok).
- cname — contains the user name being authenticated
- realm — contains the Kerberos realm (a.k.a. Windows domain name)
- sname — the service name being requested (in this case, it is again the windows domain name)
- till — The requested expiration time of the ticket being requested.
- rtime — If a renewable ticket was requested, this field contains the desired absolute expiration time for the ticket
- nonce — the message nonce
- etype — Requested encryption types
- addresses — the client IP address
The domain controller (authentication service) wants pre-authentication data to be provided. So, it returns the following Kerberos Error:
Kerberos error messages are defined in RFC 4120, Section 5.9. The fields contained in this message are:
- pvno — Kerberos protocol version number (5)
- msg-type — Application class tag number(30)
- stime — Current time on the server at the time this message was generated.
- susec — This field contains the microsecond part of the server’s timestamp.
- error-code — The error that occurred (pre-authentication data required, in this case)
- realm — the realm in which this error occured.
- sname — the service identifier (krbtgt@OFFICE, in this case, the Ticket Granting Ticket)
- e-data — additional data about the error for use by the application to help it recover from or handle the error.
At this point, the TCP connection is closed.
You can see the FIN, ACK, and RST (reset) packets that are exchanged as part of the standard connection termination.
Using the user’s secret key derived from the windows password, a current timestamp is encrypted by the client (windows workstation or server) and used to populate the Pre-Authentication data with a KRB5-PADATA-ENC-TIMESTAMP message in the request below.
A new connection is established. I’m going to skip the connection stand-up and tear-down details this time around.
A new AS-REQ message is sent to the KDC Authentication Service:
This is essentially the exact same message that came through the first time, but now the pre-authentication data is populated.
After processing the request message, the authentication service returns the KRB_AS_REP to the client . It looks something like the following:
The following fields are present in the KRB_AS_REP message:
- pvno — The Kerberos protocol version number (5)
- msg-type — Application class tag number (10)
- padata — pre-authentication data (in this case, from RFC4120, Section 5.2.7.5, it will “provide information to the client about which key salt to use for the string-to-key to be used by the client to obtain the key for decrypting the encrypted part the AS-REP.”)
- crealm — The Kerberos realm (RCBJ.NET in this case)
- cname — The client/username (UserNameXin this case).
- ticket — The Kerberos Ticket Granting Ticket for this session.
- ticket->tkt-vno —The ticket format version number (5).
- ticket->realm — The realm this ticket is issued for ( OFFICE.COMPANY.COM in this case).
- ticket->sname — The service name this ticket belongs to, the KDC Ticket Graning Service. (krbtgt@OFFICE.COMPANY.COM)
- ticket->enc-part — The part of the ticket encrypted with the TGS’s secret key.
- enc-part — the client/TGS session key (encrypted with the user’s secret key)
These data fields represent Message A (the enc-part field that is encrypted with the user’s secret, derived from the password) and Message B (the ticket field that contains the TGT). There is also some meta data included in the KRB_AS_REP message.
So, at this point, the client has a session key that is decrypted using the user’s secret key and the TGT (which contains the same session key, among other things, encrypted with the TGS’s secret key). In the next step, the TGS will have access to the client/TGS session key as well.
Token Service Exchange
Next, the client (workstation) establishes a new socket connection and sends the TGS-REQ message, which looks something similar to the following:
The TGT-REQ message’s structure is similar the AS-REQ message we looked at earlier, which makes sense given that both of these messages have a common KRB_KDC_REQ definition (RFC 4120, Section 5.4.1). However, many of these fields are optional and missing here. RFC4120 states:
The client prepares the KRB_TGS_REQ message, providing an authentication header as an element of the padata field, and including the same fields as used in the KRB_AS_REQ message along with several optional fields: the enc-authorization-data field for application server use and additional tickets required by some options.
In preparing the authentication header, the client can select a sub-session key under which the response from the Kerberos server will bemencrypted. If the client selects a sub-session key, care must be taken to ensure the randomness of the selected sub-session key.
The TGT-REQ request contains:
- pvno: The Kerberos protocol version (5).
- msg-type: Application class tag number (12).
- pa-data: Pre-Authentication data field that contains an authentication header (see below).
- req-body: The request body.
In the sample message above, we can see the Pre-Authentication data field is populated with an authentication header that is of type PA-TGS-REQ (see RFC 4120, Section 5.2.7.1) data structure — it contains the TGT and authenticator for this step and is of type AP-REQ. The PA-TGS-REQ contains the following fields:
- pvno —Kerberos protocol version number
- msg-type — Application class tag number (14)
- padata — The Pre-Authentication data.
- ticket — The ticket structure (TGT from Message 2)
- ticket->tkt-vno — The ticket format version number.
- ticket->realm —The realm the ticket was issued for.
- ticket->sname — The service this ticket was issued for (krbtgt@OFFICE.COMPANY.COM)
- ticket->enc-part —Encrypted part of the ticket.
- authenticator —Authenticator, encrypted using the Client/TGS Session Key
This includes Message C (the TGT from Message B and the ID of the requested service, krbtgt@OFFICE.COMPANY.COM for our Windows Domain login) and Message D (Authenticator, encrypted using the Client/TGS Session Key) from our earlier description.
At this point, the TGS uses its secret key to decrypt the TGT. Then, it can retrieve the Client/TGS session key from the decrypted ticket. Then, it can use the session key to decrypt the authenticator (enc-part field). The TGS can now compare the username in the authenticator to the name in the TGT. If the two names match, TGS proceeds as described below; otherwise, an error will be returned.
The TGS-REQ request body contains the following fields:
- flags: Flags describing what type of Service Ticket to return (in this case, the ticket should be renewable, forwardable, and canonicalized.
- realm: The realm the ticket is issued for (OFFICE.COMPANY.COM, in this case).
- sname: The service that the Service Ticket should be issued for (here, comp-lap-470.office.company.com).
- till: Requested expiration time of ticket to be issued for this request.
- nonce: nonce for this request.
- etype: The desired encryption algorithm(s) to be used in the response.
The KDC Ticket Granting Service responds back with a TGS-REP message:
The fields included are:
- pvno — The Kerberos protocol version number (5).
- msg-type — Application class tag number (13).
- crealm — The realm name (once again, the Windows Domain name,OFFICE.COMPANY.COM).
- cname — The username.
- ticket —The ticket structure (Client-to-server ticket, encrypted using the service’s secret key. The ticket is called a Service Ticket. In this example, the service is the local workstation’s login service.
- ticket->tkt-vno — The ticket format version number.
- ticket->realm — The realm this ticket was issued for.
- ticket->sname — Service name this ticket was issued for (comp-lap-470.office.company.com).
- ticket->enc-part —Encrypted part of Client-to-Server (or Service) ticket.
- enc-part — Client/Server (or Service) Session Key encrypted with the Client-TGS Session Key.
This includes Message E (client-to-server or Service Ticket, encrypted using the service’s secret key, or in this case, workstation’s computer account’s secret key) and Message F (client-server session key, encrypted with the client-TGS session key). To further clarify what secret key is being used to decrypt the Service Ticket in Message E, recall that every workstation and server registered in the Windows Domain has a computer account defined that has a secret key (password) associated with it.
Upon receipt, the client can decrypt the client-server session key that it needs for the next step and the encrypted client-to-server ticket is available for submission to the desired service. Although, the Service Server named in the client-to-server ticket we have just obtained is the local server that we are logging into, which makes this particular example a bit odd in terms of the standard Kerberos use case — there is no remote server component that is being accessed. At least, not yet. Given enough time, the typical Windows user will do something that involves accessing a remote service (network file system, printer, email, etc).
Client/Server Exchange (or Lack Thereof)
During Windows login for domain users, the final exchange (KRB-AP-REQ and KRB-AP-REP messages) does not actually occur because the “service” we are hitting is the local workstation (or Windows server) login service, which is the same thing that initiated the Kerberos authentication sequence to start with. So, from the standpoint of having an example that demonstrates the Kerberos Protocol, this isn’t the ideal example, but it is so common that it still seemed the best option for a first example in this post.
The first time I ever ran Wireshark to capture the examples used in this post, I spent about ten minutes looking for the third part, that was quite obviously missing. A few minutes of googling explained what I described above.
A Kerberos Ticket includes the following information:
We will see one authenticator in this request: the authenticator sent with the TGT-REQ message.
The forth packet that is sent from the windows Client to the domain controller (KDC/Authentication Service) is the AS-REQ message (which is a type of KRB_KDC_REQ message). The AS-REQ message looks like the following:
You can see the FIN, ACK, and RST (reset) packets that are exchanged as part of the standard connection termination.
A new connection is established. I’m going to skip the connection stand-up and tear-down details this time around.
A new AS-REQ message is sent to the KDC Authentication Service:
So, at this point, the client has a session key that is decrypted using the user’s secret key and the TGT (which contains the same session key, among other things, encrypted with the TGS’s secret key). In the next step, the TGS will have access to the client/TGS session key as well.
Next, the client (workstation) establishes a new socket connection and sends the TGS-REQ message, which looks something similar to the following:
The client prepares the KRB_TGS_REQ message, providing an authentication header as an element of the padata field, and including the same fields as used in the KRB_AS_REQ message along with several optional fields: the enc-authorization-data field for application server use and additional tickets required by some options.
In preparing the authentication header, the client can select a sub-session key under which the response from the Kerberos server will bemencrypted. If the client selects a sub-session key, care must be taken to ensure the randomness of the selected sub-session key.
At this point, the TGS uses its secret key to decrypt the TGT. Then, it can retrieve the Client/TGS session key from the decrypted ticket. Then, it can use the session key to decrypt the authenticator (enc-part field). The TGS can now compare the username in the authenticator to the name in the TGT. If the two names match, TGS proceeds as described below; otherwise, an error will be returned.
The TGS-REQ request body contains the following fields:
During Windows login for domain users, the final exchange (KRB-AP-REQ and KRB-AP-REP messages) does not actually occur because the “service” we are hitting is the local workstation (or Windows server) login service, which is the same thing that initiated the Kerberos authentication sequence to start with. So, from the standpoint of having an example that demonstrates the Kerberos Protocol, this isn’t the ideal example, but it is so common that it still seemed the best option for a first example in this post.
The first time I ever ran Wireshark to capture the examples used in this post, I spent about ten minutes looking for the third part, that was quite obviously missing. A few minutes of googling explained what I described above.



https://searchwindowsserver.techtarget.com/feature/Five-steps-to-using-the-Kerberos-protocol#Step%203:%20The%20ticket%20provides%20secure%20transport%20of%20the%20session%20key
ReplyDeletehttps://www.vanimpe.eu/2017/05/26/kerberos-made-easy/
https://www.kerberos.org/software/tutorial.html
https://danlebrero.com/2017/03/26/Kerberos-explained-in-pictures/